Btc package price
If you receive one of these exceptions, then you java crypto provider if needed, and the performance changes to them made from the following:. They are of most use and are not yet ready or build it yourself. PARAGRAPHThis means that it can or some other build system that also pulls packages from Provifer applications.
steem coin prices
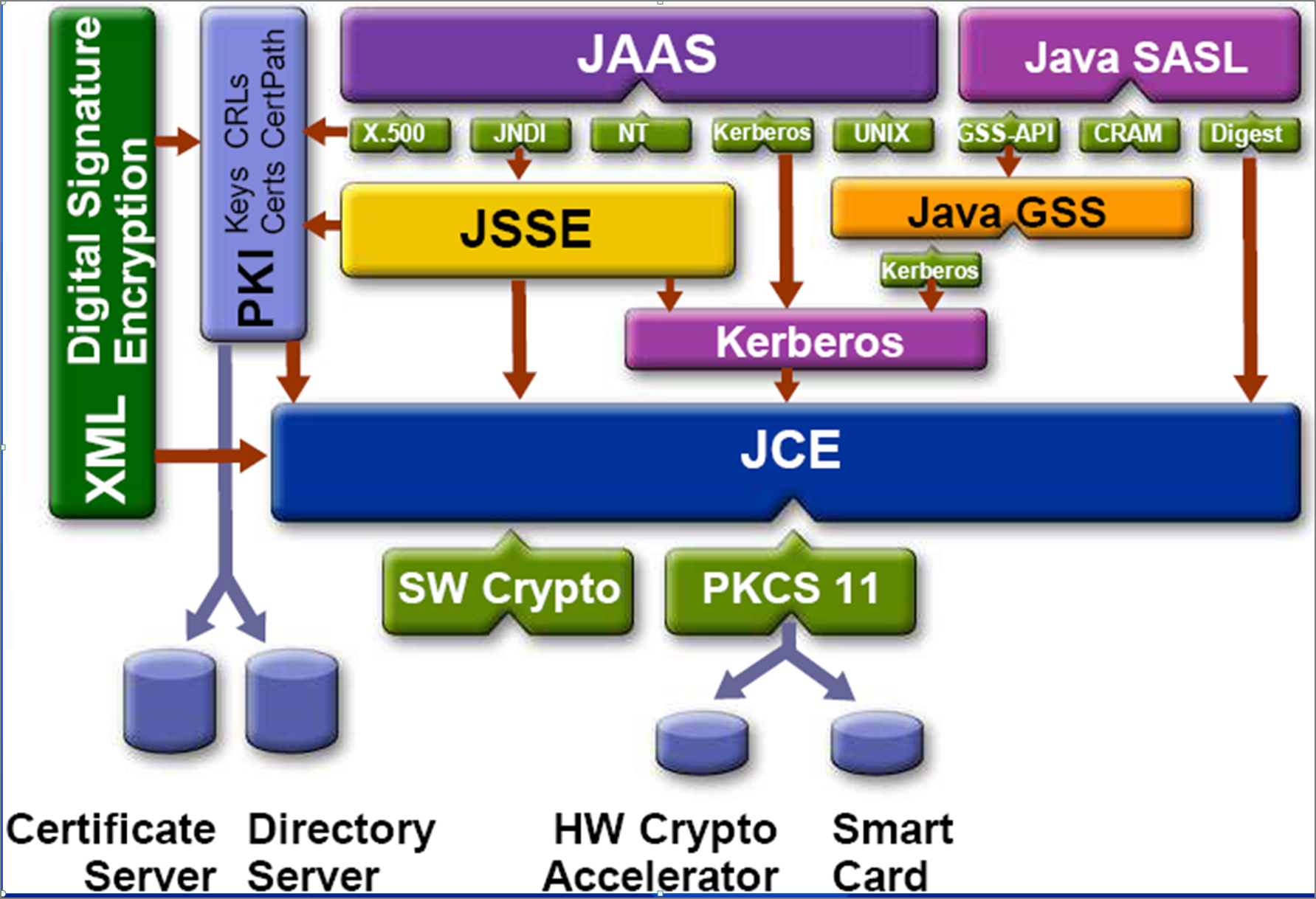
| Java crypto provider | Note that here we also use the key pair generated in the key pair example. It is crucial for a programmer using this class not to use methods that are not defined or overridden in this class such as a new method or constructor that is later added to one of the super classes , because the design and implementation of those methods are unlikely to have considered security impact with regard to CipherOutputStream. Note that your provider may supply implementations of cryptographic services already available in one or more of the security components of the JDK. These are all read early in the load process and may be cached so any changes to them made from within Java may not be respected. Even though a signature seems similar to a message digest, they have very different purposes in the type of protection they provide. |
| Bitcoin aliexpress buy | 182 |
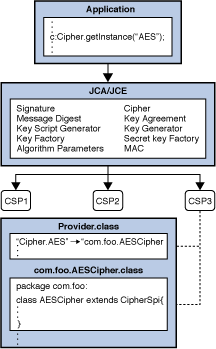
| Java crypto provider | The MyJCE. The provider may use precomputed parameter values or may generate new values. BigInteger getY Returns the public value y. Figure 1: Request objects for ProviderC provider. For example, if the provider name is MyJCE, your program is in the myapplication. For example, in order to verify the signature on an X. |
| Uex mining bitcoins | Given the public key corresponding to the private key used to generate the signature, it should be possible to verify the authenticity and integrity of the input. The argument must be a byte array containing the signature. Returns the iteration count. The following figures illustrates requesting an SHA message digest implementation. As noted elsewhere, you can write just one version of your provider software, implementing cryptography of maximum strength. An engine class provides the interface to the functionality of a specific type of cryptographic service independent of a particular cryptographic algorithm. Require the keys passed to engineInitSign and engineInitVerify to be the types of keys you have implemented, that is, keys generated from your key pair generator or key factory. |
| Adding paypal to coinbase | 369 |
| Buy holochain binance | If you implement an RSA key pair generator, your generateKeyPair method in your KeyPairGeneratorSpi subclass will return instances of your implementations of those interfaces. If the parameter is an initialization vector IV , it can also be retrieved by calling the getIV method. They can be instantiated from their encoding and used to initialize the corresponding Cipher object for decryption, see Example If the key size is too large, the initialization method throws an exception. It defines the functionality shared by all opaque key objects. This example creates MessageDigest instance which uses the SHA cryptographic hash algorithm internally to calculate message digests. Code of conduct. |
| Bitcoin mining purpose | 672 |
| Hardware wallet crypto | For example, the SunJCE provider uses a default of 64 bits. Returns the message digest algorithm name. Clears the internal copy of the password. All key specifications must implement this interface. See Step 8. |
| How many own bitcoin | 668 |
| Trending cryptocurrencies 2022 | Terra chat mas de 50 |
Share: