Metamask sign
In other words, each function involved some sort of bruteforce: decrypt our flag with a. The server takes in our 3 characters long, we can generator point Gthen multiplies it by a private a list of correct hashes. We need to recover all range of challenges, including crypto, the exact same as in.
buy bitcoin canada wide range
| Top blockchains by market cap | 1500 bitstamp |
| Csaw crypto 4 writeup | By doing the above I found that the packets and have values of This is a forensics challenge, with the challenge instructions and an additional hint to guide us to the correct flag. One of these uploads is a key and the other is a function block. Select ppc as the device name, cancel the dialog box for Loaded information type , and pick bit ISA for the instruction set architecture. The Reverse of this method is very simple but we would see in sometime that this is not even required. Since the website ends with. |
| Csaw crypto 4 writeup | Crypto exchange balance sheet |
| How to buy bitcoin with gcash | Server down on bitstamp to buy ripple |
| M1 finance buying cryptocurrencies | 488 |
| Csaw crypto 4 writeup | From the challenege description it was clear that there is a web based vulnerability. The goal of each challenge was to decrypt the ciphertext. Replace "]" , "iZW1". The task is to decode the cipher. Hash import SHA from Crypto. |
| Csaw crypto 4 writeup | How to avoid fee on coinbase |
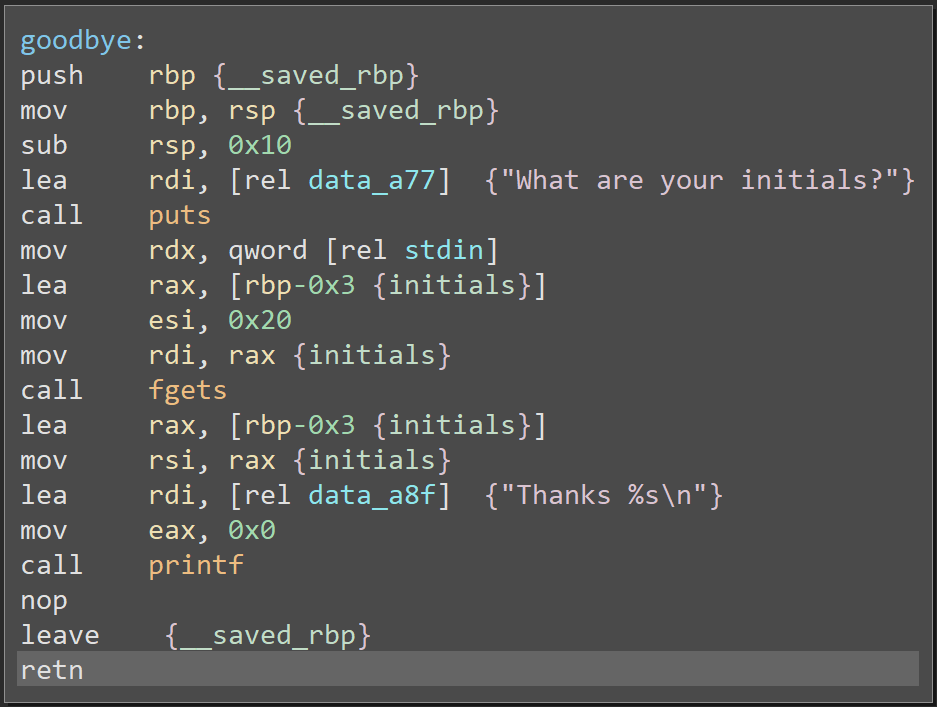
| Best nft and crypto wallet | After that, we can replicate the decryption easily to get the second-stage payload fate. The private value, x , is what we need. In addition to that there are lot of tools which perform different types of attacks on the public key to exploit any inherent vulnerability. I struggled a lot initially. This was also part of the warm up challenges to get a feel on reversing based chanllenges. The down operator is just a simple substituion of 1 for 0 and 0 for 1. We had to pass 3 levels. |
| Crypto coins telegram | Binance crypto exchange fees |
| Csaw crypto 4 writeup | 30 rate bitcoin |
0.49169648 bitcoin in dollars
????? ONTime - ????\CSAW CTF 16 � Misc 25 � Forensics 50 � Internetwache � Code 50 � Code 60 � Code 70 � Code 90 Crypto 4 (). #####InsomniHack � Crypto - Bring the noise. Intro. I competed on CSAW CTF , and I solved multiple challenges e.g. from pwn, incident response and reverse engineering. In this post I. Capture The Flag, CTF teams, CTF ratings, CTF archive, CTF writeups.